Visible Tools for Invisible Attacks
No single-point security solution will provide your business enough data protection. Backed by security and operational experts, a holistic defense-in-depth approach allows you to reduce risks and shield your data from lurking threats.
STS offers multiple security options to help build the most comprehensive security solution for your business. In addition to security services, our experts will also assist in compliance and audit reviews to help you reach even the most stringent standards. See how we can help you modernize your security infrastructure keeping your business running efficiently, and affordably.
Learn more about how your company can benefit from cybersecurity and cyber resilience efforts during this on demand webinar. Click here to watch.
Multi-Layer Security Approach
Six layers of security protection options for your business
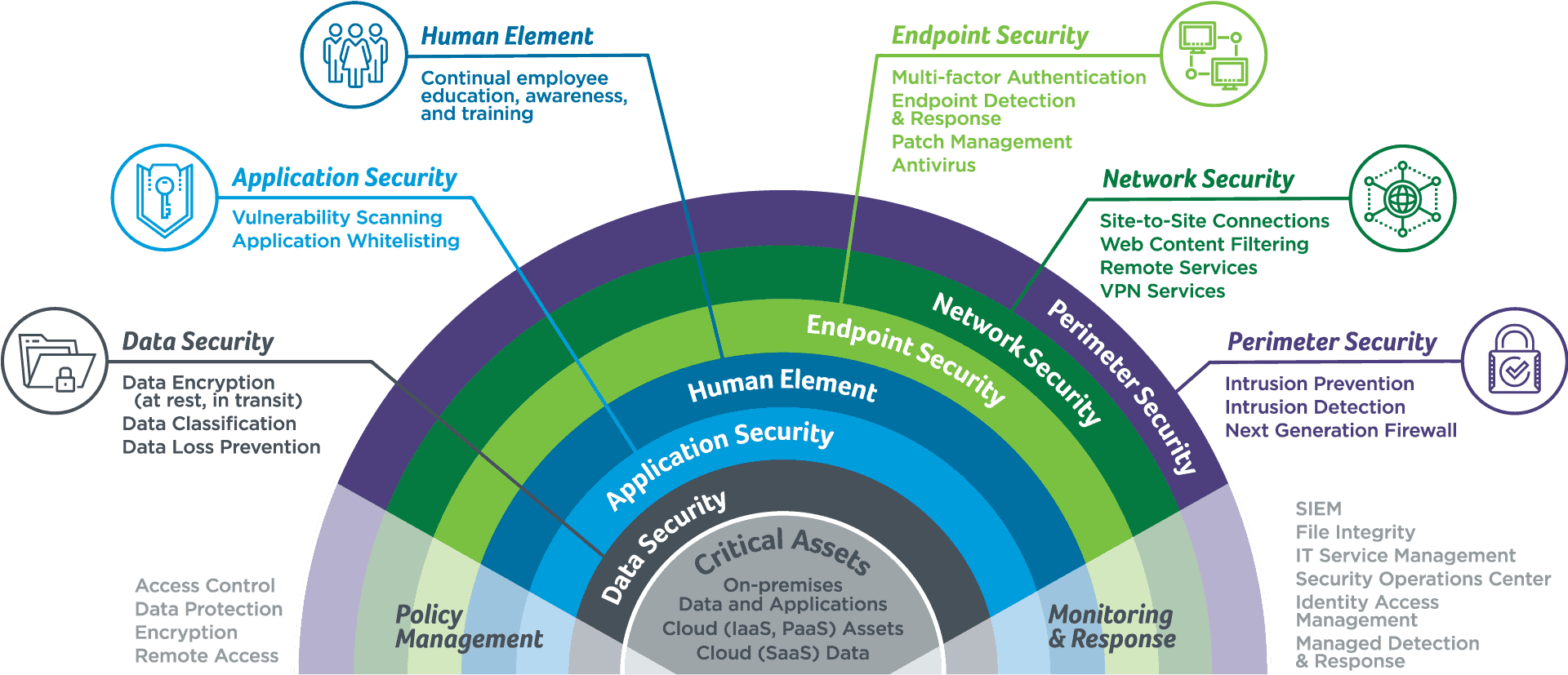
The Human Layer: Employees are our first line of defense when warding off attacks. Continually educate and train your entire staff with the help of STS.
Perimeter Security: Behavior monitoring detects and alerts you to any suspicious activity using Intrusion Prevention Services (IPS), Intrusion Detection Services (IDS), and Next-Generation Firewall Services.
Network Security: Rules and configurations to secure accessibility and integrity. STS offers Site-to-Site Connections, Web Content Filtering, Remote Services, and VPN Services.
Endpoint Security: Get real-time protection with Multi-Factor Authentication (MFA), Endpoint Detection and Response, Patch Management, and Antivirus Services
Application Security: Every time you deploy new application features or update existing ones, your security measures need to adapt. Vulnerability Scanning and Application Safelisting help secure your applications
Data Security: Data encryption (at rest, in transit), data classification, and data loss prevention are three services STS offers to help keep your most valuable asset safe – your data
Policy Management: Manage the rules and procedures everyone must follow when accessing and using your IT assets and resources with Access Control, Data Protection, Encryption, and Remote Access
Monitoring and Response: It is critical to monitor, detect, contain and remediate attacks. Through tools like SIEM, File Integrity, IT Service Management, Security Operation Center (SOC), Identity Access Management and Managed Detection and Response STS has the security solutions you need for better security protection.
Assess and Audit
Security Assessment
No more wondering, “am I protected” when it comes to your company data. STS assesses your environment to make sure you have the proper security layers aligned with your business. You can stop overpaying for unused services or implementing the wrong services, which could leave you and your data exposed to threats.
Security Audits
Regular audits help identify any areas that may have become vulnerable to hackers.
STS will conduct regular audits to make sure your security services are evolving as your business grows. In addition, we offer audit assistance for companies who must adhere to high compliance standards like HIPAA, FISMA, FFIEC, PCI-DSS, FERPA, GLBA, and others.
Talk to a Security Expert
Protect Your Data from Threats
Highlighted Security Solutions
Learn more about our security solutions.





