Regardless of your organization’s size or the capacity of your IT resources, you’ll be subject to attempted data breaches and many other security risks. Through our comprehensive environmental assessment, strategic planning, exhaustive policy review, and continuous monitoring, you can reduce risk and improve security without investing in a large security team and high-level security infrastructure.
Are you subject to privacy regulations such as HIPAA, FISMA, FFIEC, PCI-DSS, FERPA, GLBA, or others? Most firms are subject to one or more of these. A thoughtfully conceived and well-managed cybersecurity model can help you meet and exceed regulatory requirements and reduce time spent reacting to threats and exposures.
A Trusted Advisor with a Comprehensive Plan
Total Network Security
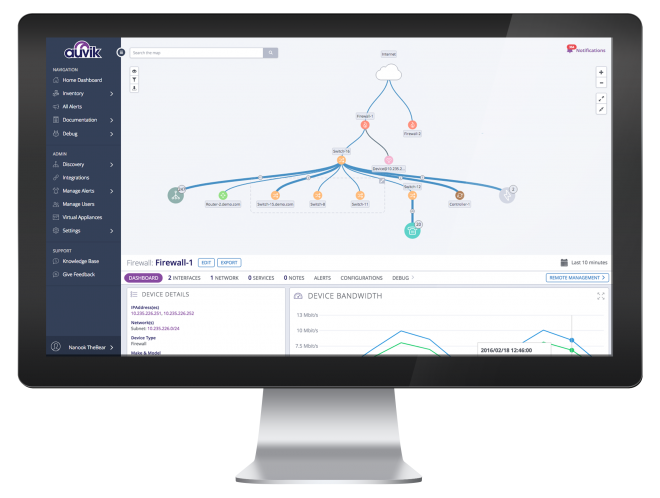
Managed risk enables you to discover, benchmark, and harden your environment against digital threats. Managed risk goes beyond software defects that traditional vulnerability assessment tools cannot identify across your networks, endpoints, and cloud environments. Internal vulnerability scanning and external vulnerability scanning services deliver the tools and expertise to continually monitor your environment, alert on threats, reducing the likelihood of an attack on your network and environment.
With decades of experience in serving highly regulated industries, our team of in-house experts stays current on the latest threats, the most effective devices and software, and the best methods to mitigate risk. We continuously apply this knowledge across all of our supported customers.
Benefits
- Better compliance exam readiness and responsiveness
- Centralized operating approach to security for improved oversight and management
- Enhanced or new security policies
- Proactive detection and mitigation of items that could lead to a breach
- Larger security footprint
State of the Art Network Management
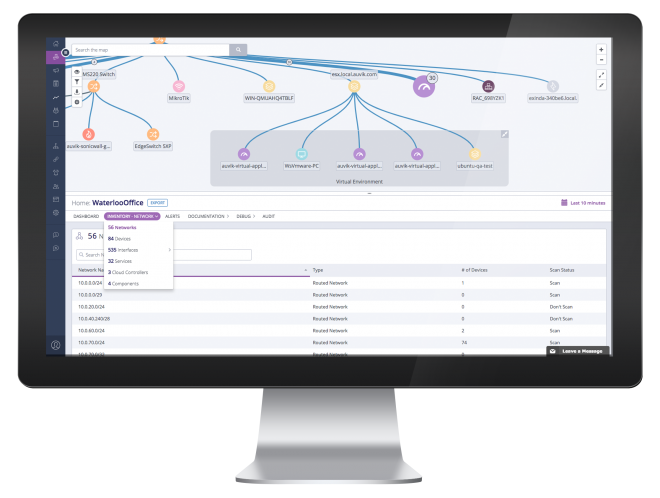
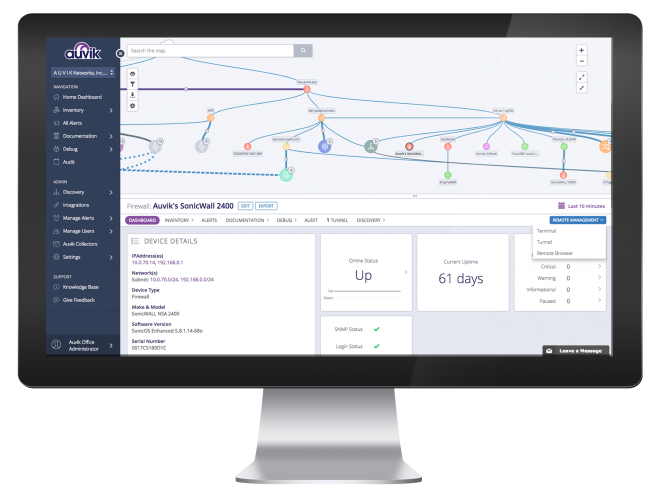
We use sophisticated network management tools for monitoring, reporting, alerting, and configuration management.
Data Breach Costs
The average ransomware fee paid in 2020 was $200,000.
Typical Engagement Steps
Security Audit
A Managed Security Services engagement typically begins with an assessment of your current security posture and a comparison to best practices and standards. This includes capturing the current inventory and topology of your network and devices and a review of your stance with regards to security audits, training, and integration of new knowledge.
Policy Engagement and Infrastructure Assessment
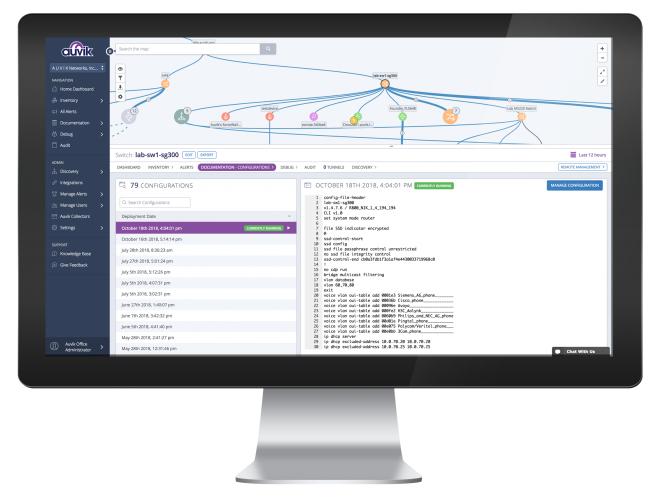
We examine your policies and procedures, baseline your IT infrastructure and its security posture, then make recommendations to update and bring them current if necessary. This includes discussion and documentation of your patching and versioning processes, access rights, and change and configuration management processes.
Strategic Security Training & Continuing Education
We create a strategic plan that will both aid you in adapting to emerging and continuous security threats and better prepare you for regulatory oversight. This can include security training for your staff and ongoing education to strengthen your security posture.
Vulnerability Scanning & Monitoring
Finally, for ongoing and proactive security, we periodically scan for vulnerabilities and deploy advanced network monitoring. Easy-to-use reporting and analysis will help you address exposures and gain valuable insights into the health and performance of your network over time.